
Stay informed on emerging ATM and ITM attack methods and the latest security recommendations to keep your financial institution protected.
ATM Jackpotting
While ATM “jackpotting” is a hot topic, it doesn’t refer to a single method of attack. Instead, jackpotting encompasses multiple cash-out techniques, each requiring distinct prevention strategies. For example:
attack:
Offline Malware Attacks have criminals extracting the hard drive from an ATM and locally loading malware onto the device. The compromised hard drive is plugged back into the ATM and used to quickly cash-out the machine.
solution:
Hard disk encryption, a protection available through DBE’s Encompass Secure service, can thwart offline malware-based cash-out attacks but won’t stop man-in-the-middle attacks.
attack:
Man-in-the middle (MITM) ATM attacks are also known as a Host Spoofing Attack. A device is placed in the ATM that impersonates the host and authorizes transactions to cash-out the ATM. When an institution has fallen victim to a MITM attack, you may hear it also referred to as jackpotting.
solution:
TLS 1.2 encryption established between the ATM and your host network prevents man-in-the-middle attacks but doesn’t protect against offline malware-based cash-outs attacks.
ATM Protection Recommendations:
No single countermeasure can prevent all types of attacks. As bad actors continue to innovate their attack methods, protections must also adapt and evolve making a layered ATM security approach essential.


Reduce Risk with Encompass Secure from DBE
Encompass Secure offers full hard disk encryption and whitelisting, protecting against offline malware cash-out attacks, one of the attack methods commonly referred to as “jackpotting”.
We’ve intentionally kept the price point low and implementation time quick, to make this essential protection accessible for our clients.
Encompass Secure is available now for NCR units and in testing for Hyosung machines. Click here to learn more about Encompass Secure
Learn More About SecureMitigating Skimming Risks
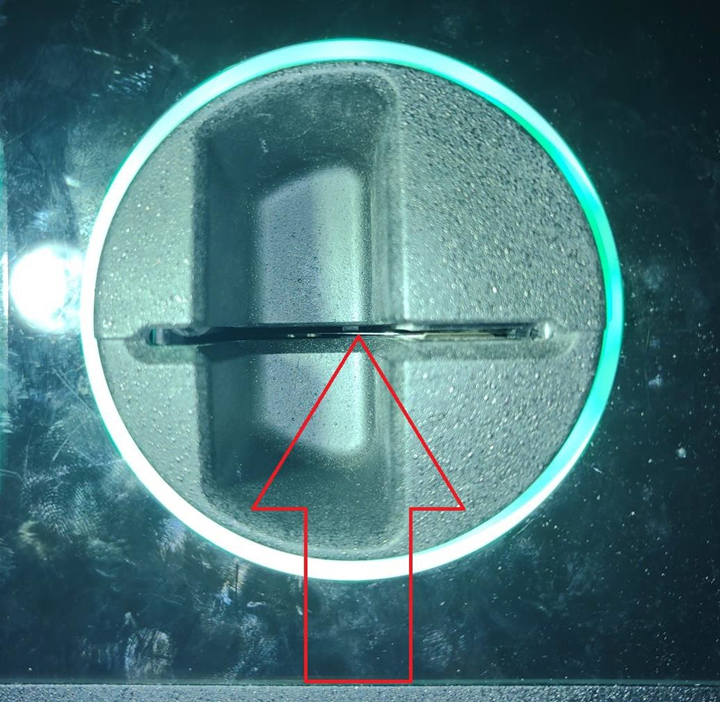
Card skimming remains a significant concern due to the ease with which criminals capture and exploit static Track 2 data from magnetic stripe cards.
Skimming Protection Solution (SPS) and Tamper Detecting Card Reader (TDCR) are two effective tools to reduce skimming risk. In today’s environment, ATMs and ITMs require both SPS and TDCR, as each addresses a distinct skimming threat.
SPS combats external/overlay skimmers and has been standard on all ATMs ordered from DBE since 2017.
TDCR addresses ultra-thin, deep insert skimmers. DBE made TDCR standard on all new 80 series models since late Q3 of 2023 when it became available to order. If you’re unsure whether your ATM has a TDCR, reach out to your DBE salesperson. We can confirm and provide a field upgrade quote if needed.
Upgrade to Activate Enterprise Software and enable Contactless Cards, reducing the static Track 2 data risk from magnetic stripe cards on your devices.

